
posted on 03 May 2015
The following are notes collected from a deep-dive investigation into a hard-disk image that was shipped from Japan. The image appears to have come from the original manufacturer unmodified.
This investigation does not cover any information about reverse-engineering the game binaries or decrypting the game data.
Research performed on SPADA (iidx21) legitimate hardware unless mentioned otherwise.
USB Keys
The USB security keys are attached to the back of the machine via a two-port USB hub. They are iKey 2032 Two-Factor USB Authentication Tokens. One appears to be used for decrypting game data and executable files (“LICENSE KEY”), while the other appears to be used for verifying e-AMUSEMENT participation with Konami servers (“ACCOUNT KEY”).


The security keys are protected with a passphrase that is presumably hard-coded in the game executable or operating system config files. The iKey driver will lock out access to the security key if too many failed attempts at the passphrase are detected.
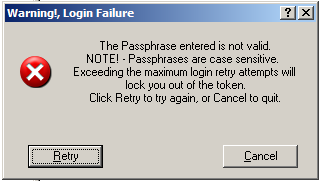
LICENSE KEY
Utility can access KONAMI root CA and public signing key. Utility output can be viewed here.
Hard Disk
The hard disk used is a WD 320GB 2.5” drive with the following label on it: LDJ-JA beatmania IIDX20. Presumably the drive that I have was included in a Tricoro (iidx20) kit, and at some point the contents were upgraded to SPADA without replacing the original HDD.

Drive Content
The drive contains a mixture of encrypted and unencrypted data. All of the game data, shared libraries, and executable files are encrypted.
The directory structure of the LDJ directory (where game content is stored) differs between the stock installation and the one distributed by programmedworld.
programmedworld LDJ Directory Structure
- C:
- OS partition. Contains program files, windows dir, etc.
000ROM.txt- Contains single string: “LDJ-JA-A01 2012-03-22 0”
- Possibly metadata about the game version contained on the hard drive
boot.ini- Windows configuration file with options related to loading operating system data.
[boot loader] timeout=0 default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS [operating systems] multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Embedded" /fastdetect /bootlogo /noguiboot
NTDETECT.COMntldrWERUNTIME.INI- not sure what this is
- D:
- Game data partition
LDJ- Main game data directory
- Encrypted
- Contains
contentsandpath.lst path.lst- CSV list of all files
- Purpose/meaning not clear
contents- Game data and encrypted executable code (dlls)
- Organized into hexadecimally numbered subdirectories (0, 1…, a, b)
- Contains:
dev,modules,prop,allfiles.lst allfiles.lst- Encrypted. Probably the same CSV file format as
path.lst
- Encrypted. Probably the same CSV file format as
dev- Appears to be application’s cache directory
- Contains log files, binary caches, XML files for bookkeeping, etc.
- All encrypted
modules- Shared libraries and executable files
- Encrypted
prop- XML files for bootstrapping
- Two “p7s” files
trustcerts.p7strustfiles.p7sP7S file usually contains DER encoded CMS (Cryptographic Message Syntax) structure of SignedData type which is defined in RFC5652. You can use ASN.1 Editor to conveniently examine exact structure and contents of your file.
- Encrypted
factory- Utility programs and shared libraries for factory testing?
systemLDJ.exe- Likely a factory test executable
- Not encrypted
wave- Sound files that play a single tone in the key corresponding to the filename (e.g. “C.wav” plays a tone in the key of C)
- 4 files in total (
C.wav,D.wav,E.wav,F.wav)
d3dx9_24.dllD3DX9_41.dll- Unencrypted builds of the DirectX library
existd- Empty file presumably indicating the existence of the drive without depending on drive letter matching
factory.bat- Script that runs the factory test executable store in
factory
- Script that runs the factory test executable store in
infodisp.exe- Looks to be a standalone program used to display error messages in a dialog box
select.bat- Script that bootstraps the game application
- Error messages localized to Japanese
- Full contents of this script (converted from ShiftJIS to unicode) can be accessed here
- Runs
update.exe - Sets up environment variables (mostly paths to resource files)
- Creates cache directories if non-existent
- Pings localhost 30 times? (redirects output to
nul)- Comment says “ドライバが安定するまで 30 秒ほど待機する”, which translates to “the driver will wait about 30 seconds to stabalize”. Sounds like a hack to workaround some bug in the iKey software.
- Runs
bootstrap.exewith the following argumentsprop\bootstrap.xmlbm2dx_drmprop\trustcerts.p7sprop\trustfiles.p7s
- Displays an error code if one was set by
bootstrap - If
bootstrapreturns a code of 0, the machine shuts down
update.exe- Unencrypted
- Presumably contacts update server to check for updates before running
bootstrap
- E:
- Partition that acts as a staging area for game updates
UPJAA2013100200- Looks to be an update that was downloaded while this kit was active on the e-AMUSEMENT network in Japan
- Contains
contents(same dir structure asLDJ\contents),LDJ131008.bsv.bak, andpath.lst - Basically an LDJ folder that is merged with the existing one
.bsvfile is probably a signature file for verifying contents
existe- Same purpose as
existd
- Same purpose as
- F:
- Empty except for
existf
- Empty except for